CMMC Assessment Procedures: When Is Enough Data Enough?
What Data Are In Scope?
You are assessing against the 171 standard using the CMMC framework. While practices require data to be separated from authorized and unauthorized users and other controls require compliance with federal regulations you assess against the assessment objectives in the CMMC Assessment Guides.
You do not perform an Assessment of the sovereignty and provenance of data. You will not look for ITAR spillage. This is an assessment against the CMMC practices using the assessment objectives from 171a.
You do not check systems to see if an Organization Seeking Certification followed through on the Incident Reporting requirements. This is not an assessment of compliance with DFARS 7012.
Now an assessor will check to see if an access control policy or if a chosen product would meet the requirements of keeping unauthorized users in compliance with export control regulations. If your CUI policy mentions 72 hour reporting requirements than An assessor may check the procedures to ensure organizationally defined times in an incident response plan would meet DFARS requirements as evidence you do what you say.
All of this gets defined in scope. This is not a NIST-SP-800-171a assessment nor a NIST-SP-800-53a assessment. It is a CMMC assessment using the CMMC Level 1 or 2 Scoping and Assessment guides. Any Organization Seeking Certification will have the right to demand they must only comply with the NIST-SP-800-171 standard as presented in the assessment guide. You can not fail, someone, nor do you even assess, if they meet the NFO controls of NIST-SP-800-171 . You perform a CMMC assessment. Period. The conditions of this assessment get finalized during scoping assessments.
Scoping Matters
What data and systems are in scope gets settled during a scoping pre-assessment. For a level 1 self assessment it is just best to assume your entire system falls in scope given the broad categorization of Federal Contract Information.
Once you know the systems and assets in scope a Certified CMMC Professional can start to help an Organization collect, or they can help as a member of an assessment team. In fact, at this time, a CCP can qualify to take a CCA exam after completing three assessments as a meber of a team.
What is an Assessment?
CMMC draws from NIST-SP -800-37 for a definition of Assessment:
The testing or evaluation of security controls to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for an information system or organization
Let us unpack this a little bit.
First their are the security requirements for the information system or organization. For CMMC this includes the requirements in NIST-SP-800-171.
Then you have a desired outcome. This is the governance evidence. Where does the OSC have it written down what should happen. This maybe company policy or software defaults. It maybe in a shared responsibility matrix it may reside in a service level agreement.
Next, working backwards, comes “implemented correctly.” Here you are checking if the procedures will do what the policy says the company will do. This could be reference architecture or implementation guidelines. Step by step guidelines to ensure the control operates as intended.
Then you may interview people to see if they do the do or watch a company test something such as a passowrd lock out after an organization defined number of password attempts.
A CMMC assessment never involves any penetration testing. Leave your lockpicks and honeypots at home. A CMMC never involves a CCP running any data discovery tools or analyzing audit logs for potential breeches. A CCP collects or evaluates evidence to make sure audit logs meet the security requirements of 171. This means knowing which secuirty requirements are applicable to which controls.
What is Applicability?
You don’t check to see the last time a cloud based MFA tool attended its last training session. Role based training requirements are not applicable to tokens nor to your key boundaries. Now to people who have privileged access the tools keeping data separated at the boundary? Role based training requirements are applicable.
When you conduct a CMMC scoping assessment the CCP and OSC will review the assets. All the assets in the end get scored against 110 requirements but many might get marked as not applicable.
NIST-SP-171a rules break down to each requirement having enough depth and coverage. If any security requirement of a CMMC practice falls in scope than you must meet the rest of the requirements to provide enough depth to ensure the practice gets met.
Once a security requirement falls in scope all the security requirements of that CMMC practice fall in scope.
For example let’s take the Maintenance domain. MA.L2.-3.7.5 requirements have you protect CUI when machines go for off site repair. If you simply replace and do not send computers off site for repair this practice and all its assessment objects would get marked not applicable.
If however you allow CUI stored on mobile devices a CCP may look for evidence that employees do not take devices into repair shops for such things as cracked screens. Now all of the determining statements of MA.L2.-3.7.5 assessment objectives are applicable.
Some Organizations Seeking Certification may seek a variance for specific controls from the 171 baseline. This would mean that they need to use offsite repair for devices with CUI but for some reason can not meet all the assessment objectives of MA.L2.-3.7.5 . In this case, they would need to ask and receive a variance from the Department of Defense CIO.
A CMMC assessor will never test if the variance gets followed. This is not a DFARS assessment. The requirements for a variance are not in NIST-SP-800-171. You may though use a document proving a variance exists as an assessment object to meet the adequacy and sufficiency requirements of the CMMC Assessment Process
What is an Assessment Procedure
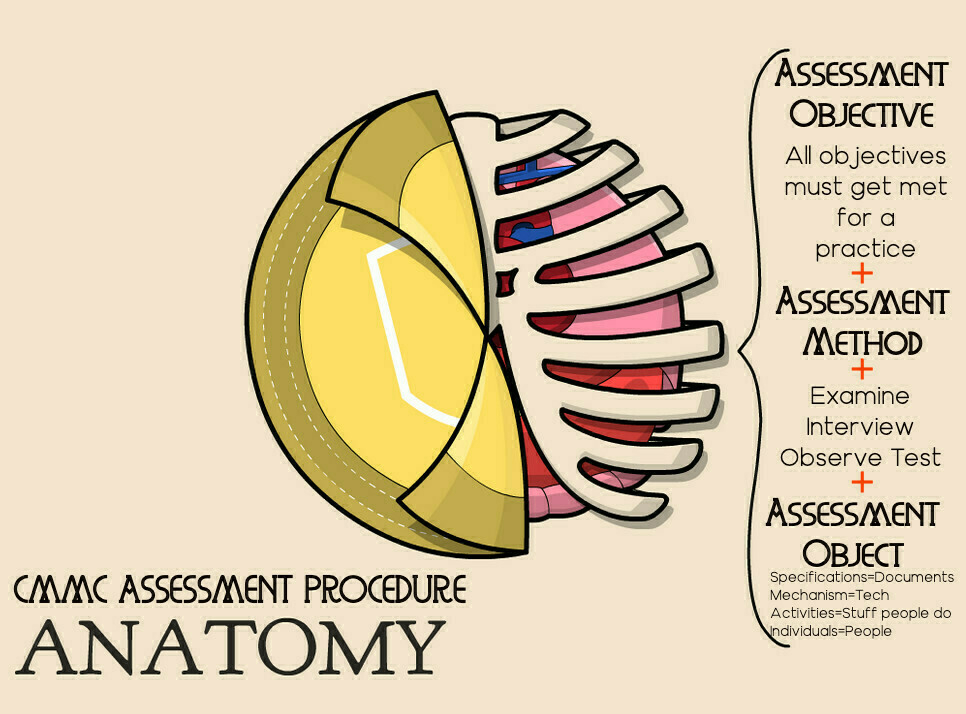
As assessment procedure gets broken down into a few parts to ensure the accuracy of the information. This includes the determining statement. This is the assessment objective of what the evidence must show is getting met. This determines traceability of accuracy of the evidence. Without accuracy the depth of the CMMC practice can not get guaranteed.
You link this content to the evidence. This evidence makes up the assessment objects. You must collect enough objects to ensure the determining statements get covered sufficiently. This helps to ensure the breadth of the practice get met.
In terms of assessment objects they come in three flavors:
What is an Assessment Object?
- specifications-Document based artifacts that explain, explicitly or implicitly (never leave anything to inference int he system security plan), how the determining statements get met. This includes, “policies, procedures,security plans, security requirements, functional specifications, architectural designs” (CMMC, 2022, pg 7).
- mechanisms-the stuff and equipment that makes up your systems. An assessor, for example may check how your patching and update mechanisms work on your antivirus software.
- activities-stuff people have to do to protect systems. This could include holding a table top exercise as part of risk awareness, bimonthly meetings to review the SSP, or your back up plans.
- People who do the activities to ensure the mechanisms meet the specifications.
What Are The Assessment Methodologies?
In terms of gathering assessment objects you utilize three methodologies. The methodology rounds out the third and final part of the assessment procedure.
- Examine-Touching assessment objects. Usually specifications and document based artifacts such as policies and procedures. This includes HR documents, Acceptable Use Policies, System Security Plans, etc
- Interview-Talking to assessment objects, but call them people. You can have discussions with individuals or groups for clarification, to suss out if procedures get followed, or to collect more evidence.
- Test This means watching the results of an activity or mechanism get performed under specific conditions. For a CMMC assessment this means an in-scoped individual will engage in the activity or mechanism. At no time does a CCP or an Assessor really need access to the CUI stored on a system. You will not test any systems.
When is Enough Evidence Enough?
CyberDi uses a claim, connect, action approach to considering if we have sufficient evidence to meet the breath of coverage necessary for each determining statement or assessment objective. You make a claim against a practice of not or met. You then connect each assessment objectives to enough to ensure someone else would reach the same conclusion reading your report.
If you are an CCP helping an Organization prepare you provide actionable feedback that can get added to a Plan of Action that would lead to the practice getting met with enough depth and breadth.
When determining the adequacy of evidence you need to consider all three assessment methodologies. For some practices you will rely on the governance documents more while other practices will require a focus on the mechanisms. The nature of the control determines how much focus you put on each of the assessment methodologies.
First you ask which of the three methodologies will provide you the greatest depth in ensuring breadth to help ensure the accuracy of of the evidence used in the assessment procedure. You consider if you need a basic, focused, or comprehensive use of the methodology against the assessment objects.
Once you decide on which assessment methods give you the greatest depth you would then increase the chances of making a correct assessment by including evidence from other methodologies but you may not apply the same level of focus to the depth of the assessment. By utilizing a mixture of assessment methodologies, and including both quantitative and qualitative evidence in your report or system security plan you ensure the adequacy of the evidence to prove the accuracy of your claims.
References:
NIST-SP-800-171a Appendix DNIST SP-800-37
NIST SP-800-18
Bonner, R. (2002). The Importance of Scoping and Applicability in CMMC. Retrieved from: defcert.com/the-impor… DefCert.
Image Credit Remixed From Bryan Mathers’s Anatomy of an Open Badge originally shared with a Public Domain license CC0